Subscribe
I recently got my hands on an ordinary-looking iPhone-to-HDMI adapter that mimics Apple’s branding and, when plugged in, runs a program that implores you to “Scan QR code for use.” That QR code takes you to an ad-riddled website that asks you to download an app that asks for your location data, access to your photos and videos, runs a bizarre web browser, installs tracking cookies, takes “sensor data,” and uses that data to target you with ads. The adapter’s app also kindly informed me that it’s sending all of my data to China.
The cord was discovered by friend of 404 Media John Bumstead, an electronics refurbisher and artist who buys devices in bulk from electronics recyclers. Bumstead tweeted about the cord and was kind enough to send me one so I could try it myself. Joseph has written about malicious lightning cables and USB cables made by hackers that can be used for keystroke logging and spying. While those malicious lightning cables are products marketed for spying, the HDMI adapter Bumstead has been found in the wild and is just another crappy knockoff cable sold on Amazon’s increasingly difficult to navigate website. This HDMI adapter is designed to look exactly like Apple’s same adapter. Here they are side-by-side:



“I don't necessarily see evidence that this is a truly predatory device, but it demonstrates well enough how one like this COULD be, and I've read about others that definitely are, that have an embedded web server, WIFI, key logger, and basically a small computer right inside the cable,” Bumstead said. “The super scary thing about this concept is that the user is basically introducing a predatory element inside their security bubble, so the device could conceivably get full access to whatever it’s plugged into.”
The pseudonymous researcher known as MG, who made the malicious Lightning cables that Joseph previously tried out, told 404 Media that he’d put this adapter in “with the risk of garbage apps as well. People will install so much sketchy stuff.”
“My gut says it’s probably non-malicious… at least not any more so than a lot of Chinese-authored apps,” he added. “I suspect it is just another Chinese knockoff device. They probably don’t have things created the Apple way, so the app works around it. Tons of the Lightning accessories on Aliexpress have you use a Chinese app.”
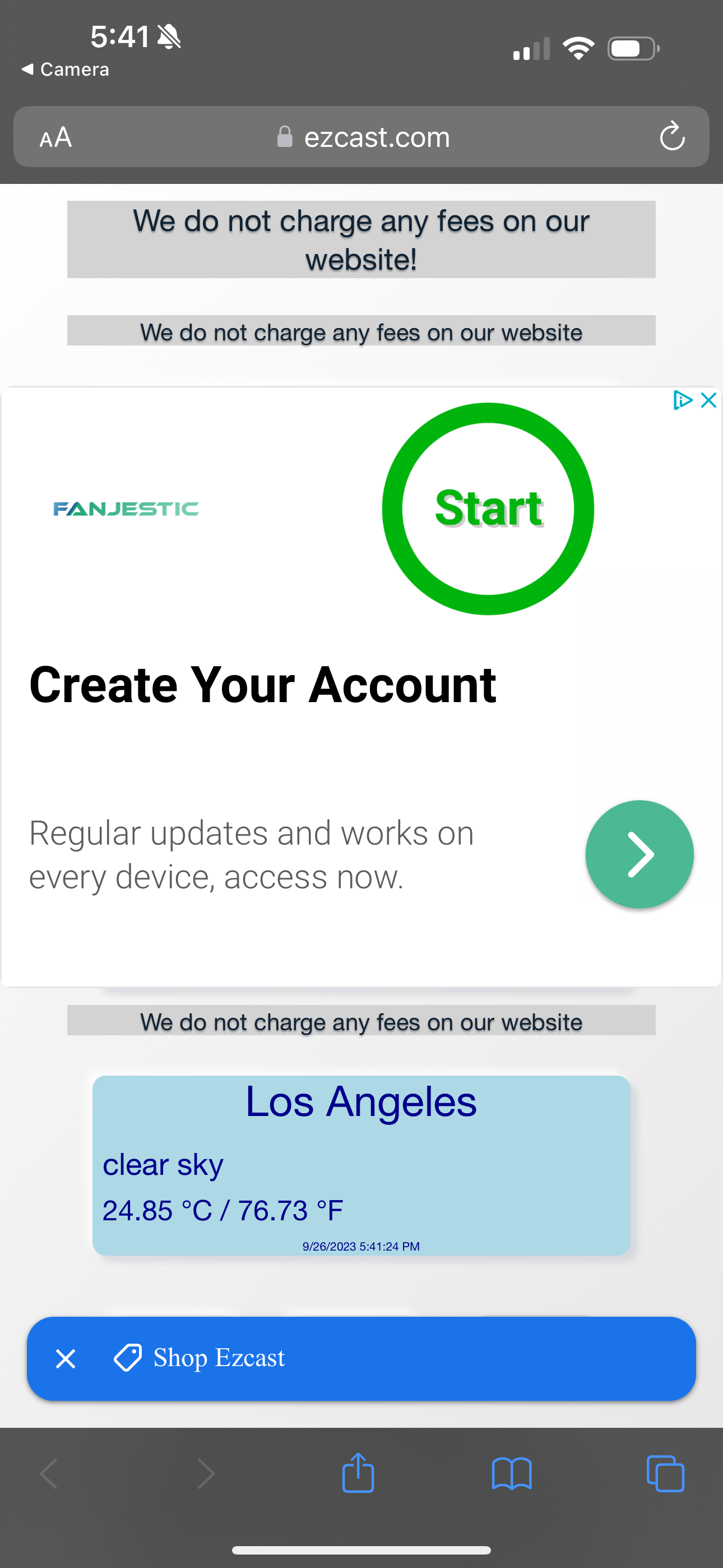
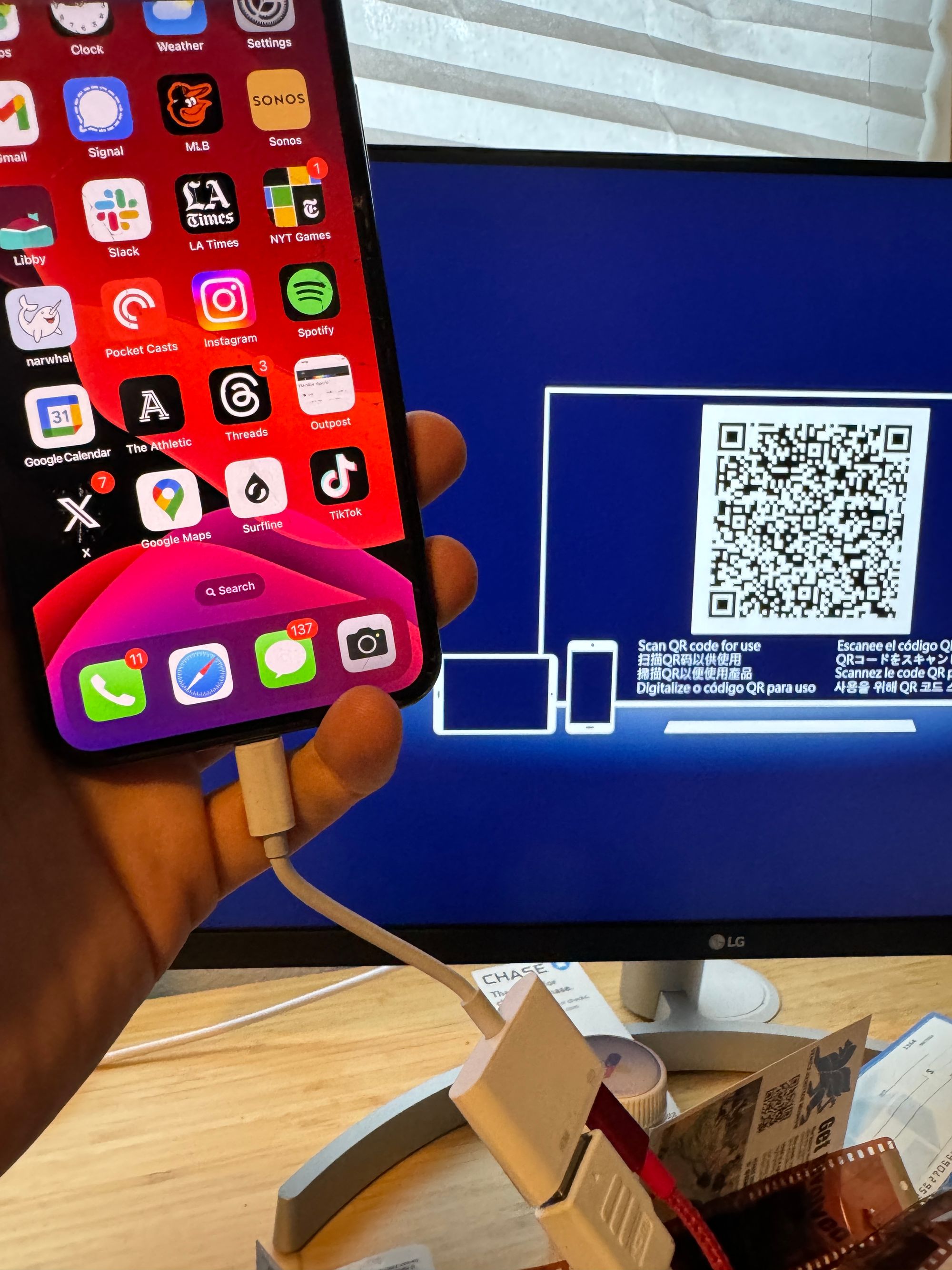
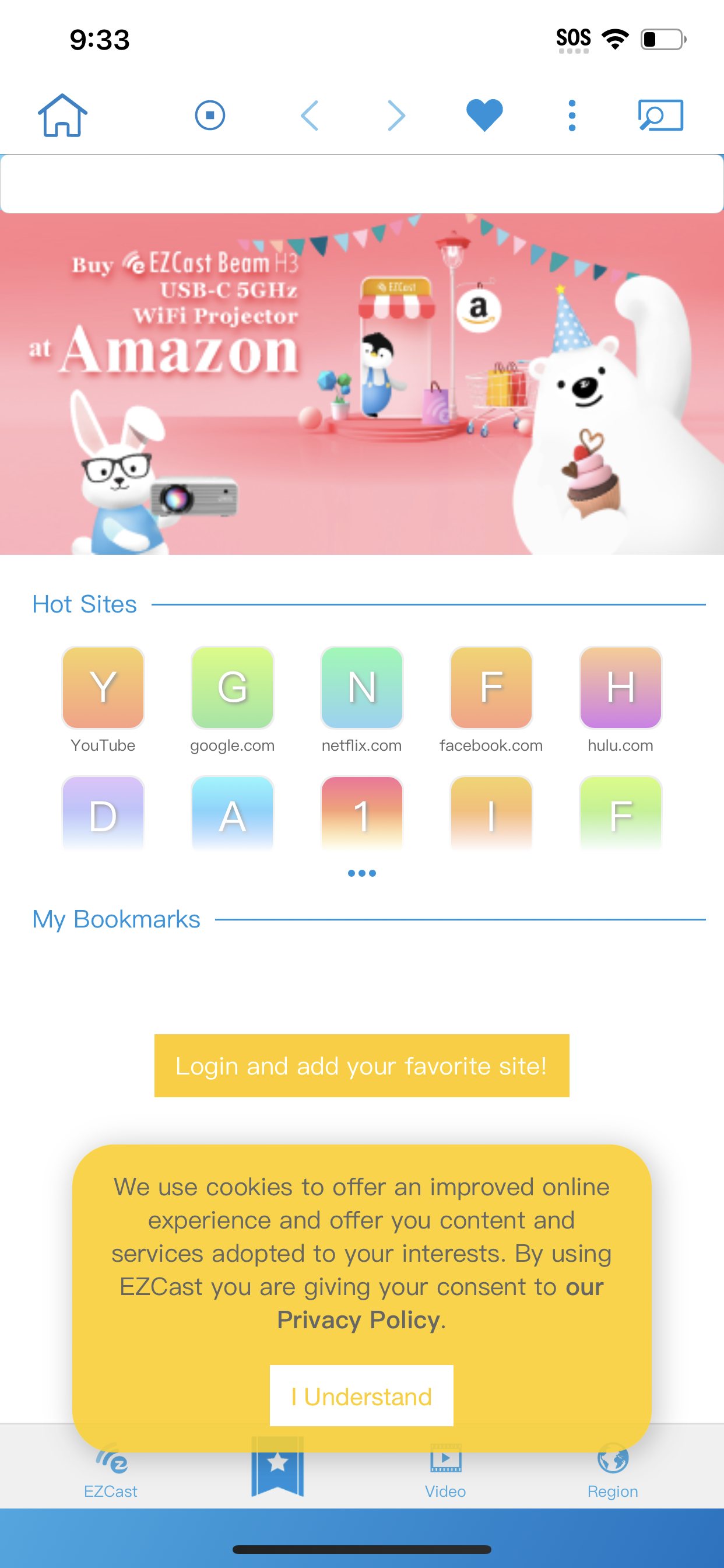
I decided to connect the cord using an old iPhone that I no longer use and that no longer has anything I care about on it. After I had powered on the adapter (it requires a separate lightning cable to power it) and connected it to my monitor, a screen with a QR code, a serial number, and the branding “LIVE TV” popped up. I scanned the cord and was taken to the website for EZ Cast, an adapter company that claims to have “more than 10M users around the world who use the complete EZ Cast solution for work and leisure applications.”
Cybersecurity firm Check Point previously analyzed what it described as an “EZCast dongle.” The company found it was easy to brute force the device’s 8-digit numeric password. Check Point writes it contacted EZCast about its findings back in 2016, but did not receive a response. “The EZCast device was never designed with security in mind,” Check Point writes.
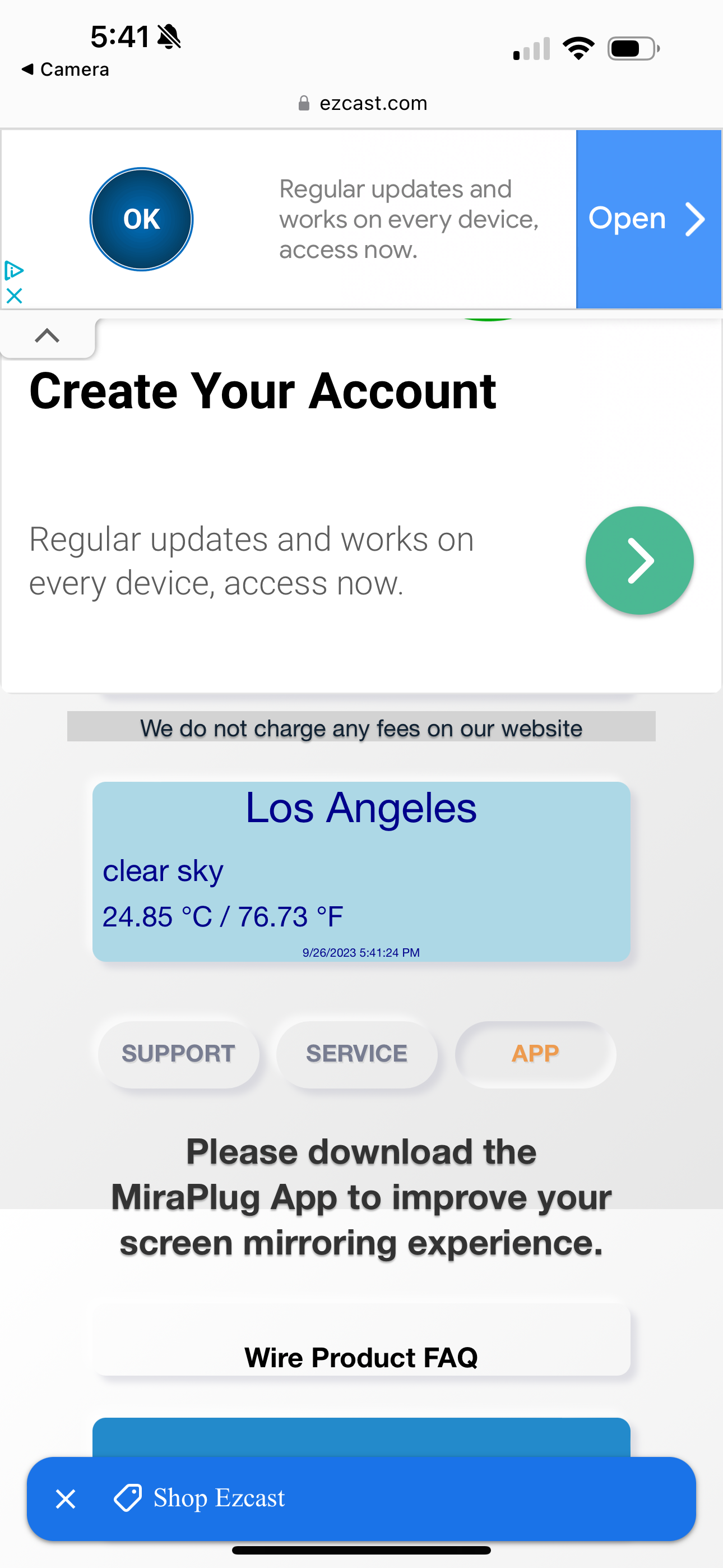
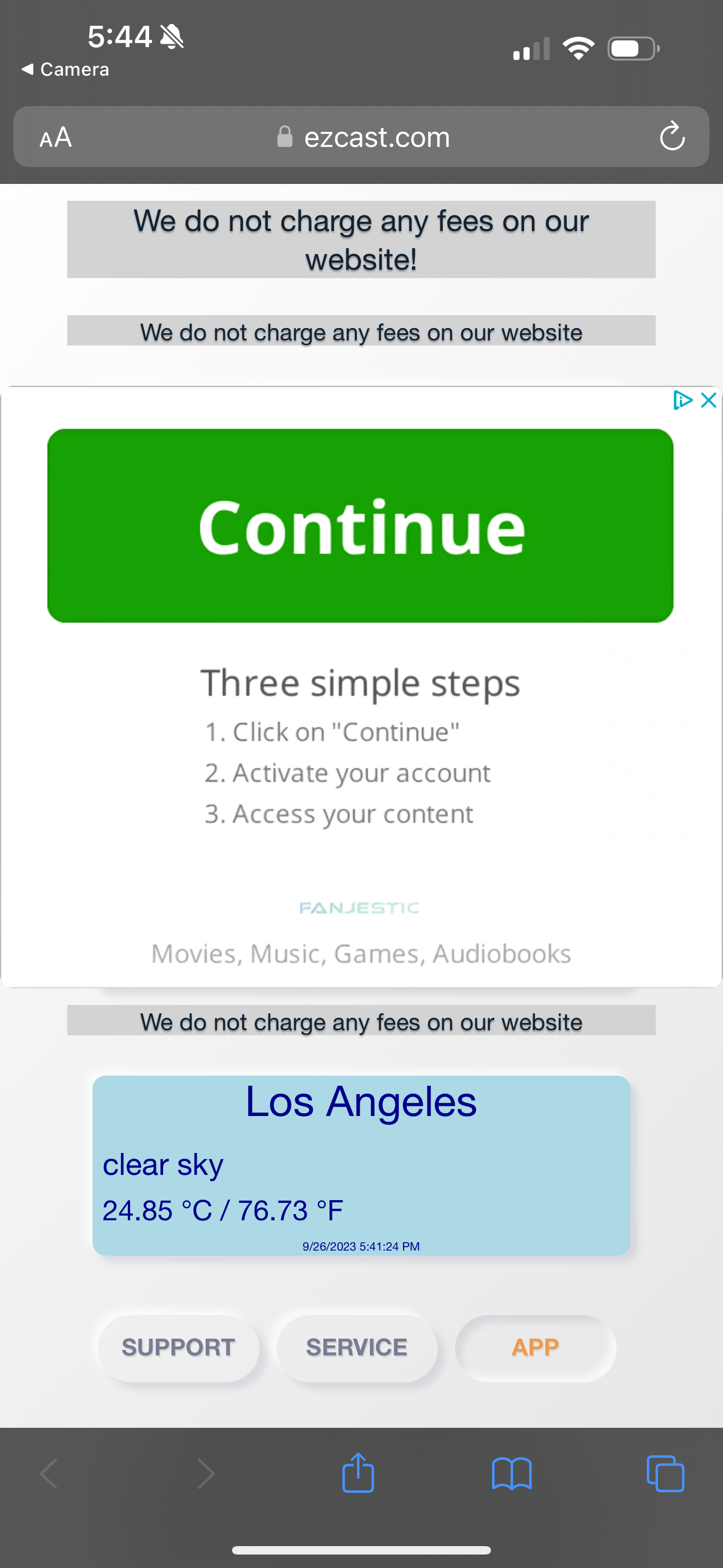
The portal has a headline that says “We do not charge any fees on our website!” and displayed an ad for something called “FANJESTIC,” which is ostensibly a streaming service that the company is trying to get users to sign up for (and does indeed require a credit card, and costs $49.95 a month). The site MalwareTips.com has identified this as an autobilling site that is difficult to cancel. FANJESTIC is not the same as the EZ Cast app that the QR code ultimately got me to download in order to use it. The QR code page also has an infographic that implores me click “Trust this computer” when I plug my iPhone in (an ordinary HDMI cable should not be detected as a “computer,” for what it’s worth).
Because I enjoy living dangerously, I did plug my phone in, unlocked it with my passcode, trusted the “computer” and let the website take me to the App Store, where I downloaded the EZ Cast App, which has a 2.1/5 rating and 878 reviews. Example reviews: “It’s not working.” “Useless and frustrating.” “Why go through all this trouble for a mirroring device?” “I don’t understand why I have to buy an app from a third party company to use what looks to be an apple product in appearance” “SCAM!” “Doesn’t work,” “Don’t fall for this app at a karaoke machine,” “Totally fake … It makes me suspicious of Spyware. This App and the cable = JUNK.” Some of the reviews said they bought the cable from Amazon, another mentions it came from Walmart, another mentions eBay.
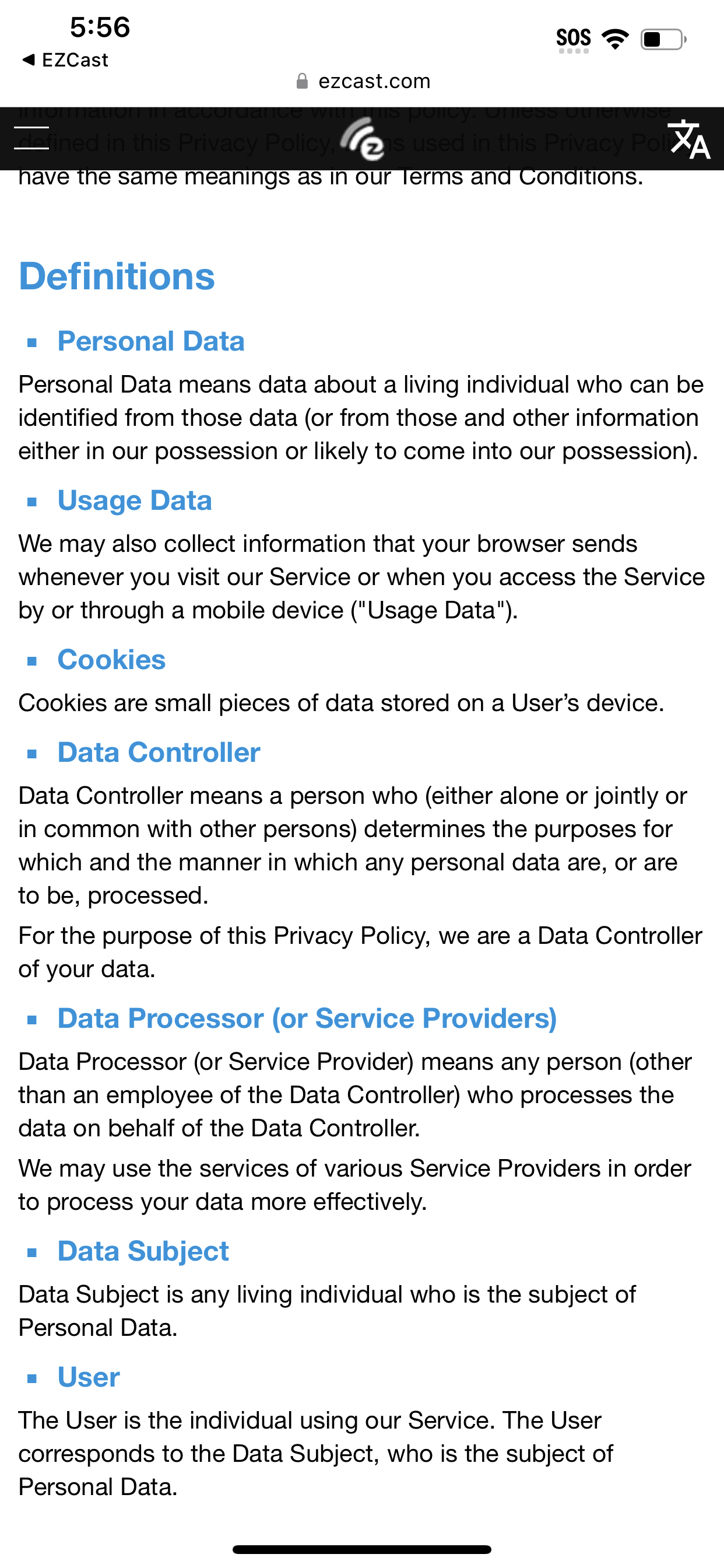
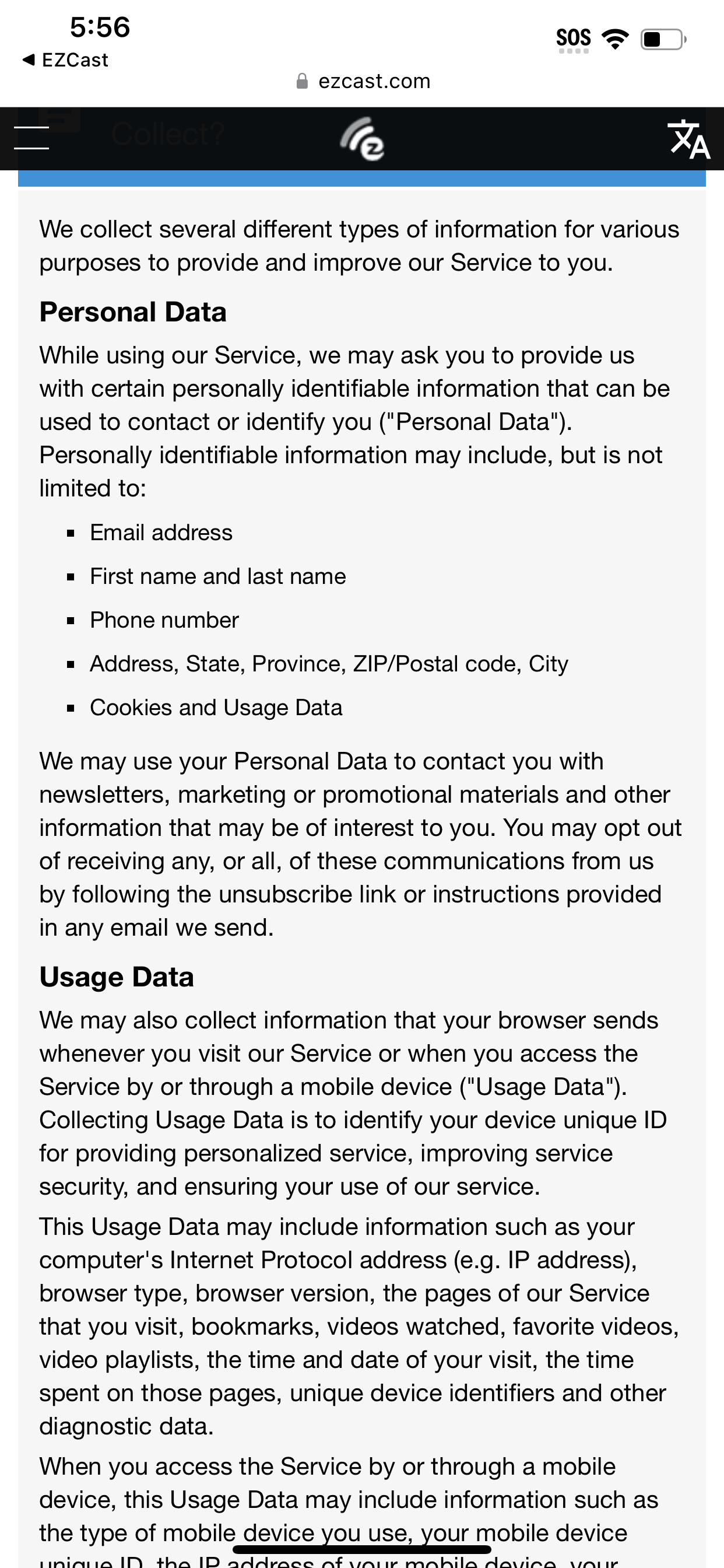
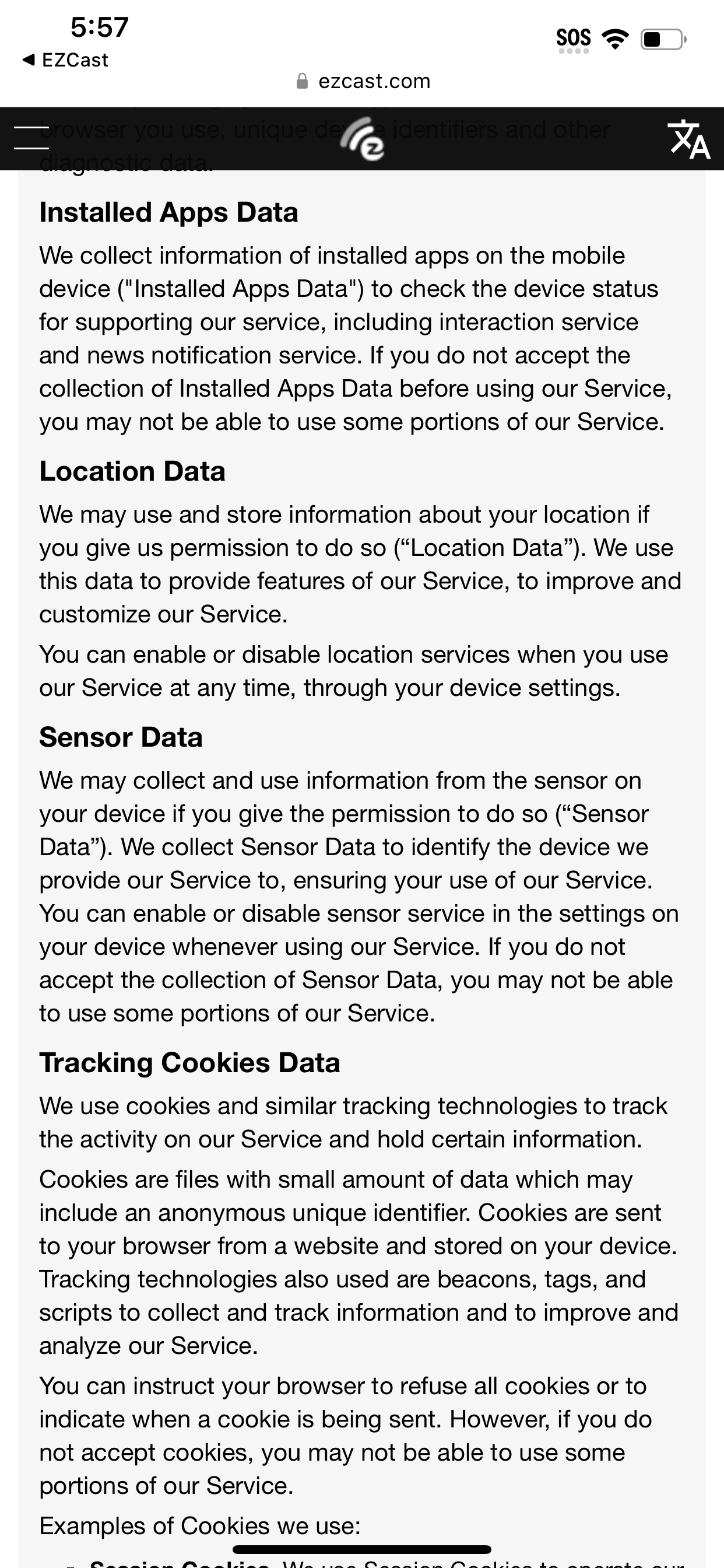
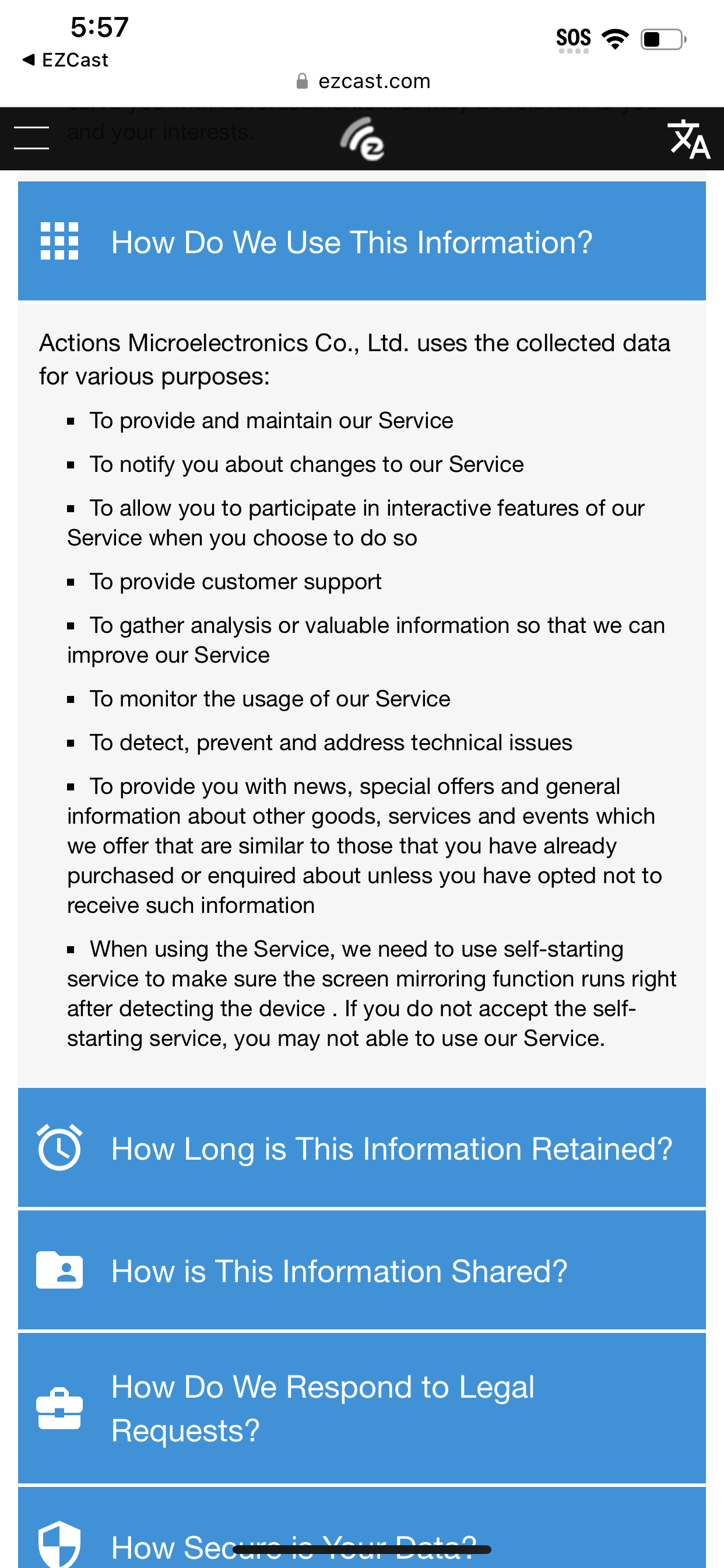
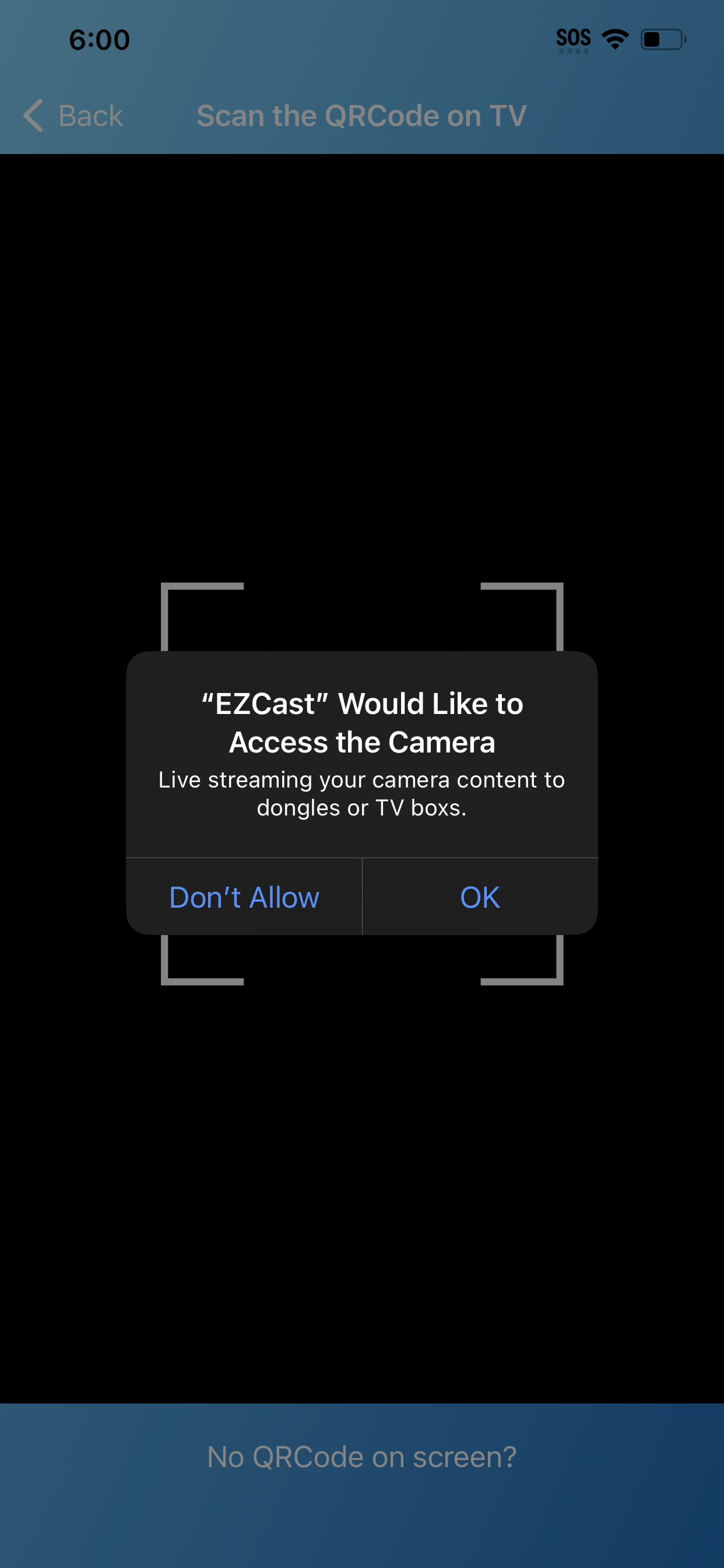
After opening the app, I was immediately prompted to give EZ Cast my location and to accept a Privacy Policy from a company called Actions Microelectronics Co., Ltd. that says EZ Cast would be collecting my email address, use tracking cookies, take my location, track my “favorite videos, videos watched, and bookmarks,” as well as “Location Data, Sensor Data, Tracking Cookies Data, Installed Apps Data,” and would be using that data to target ads to me. It also required access to my Local Network, asked for access to my photos, settings, Bluetooth, and camera.
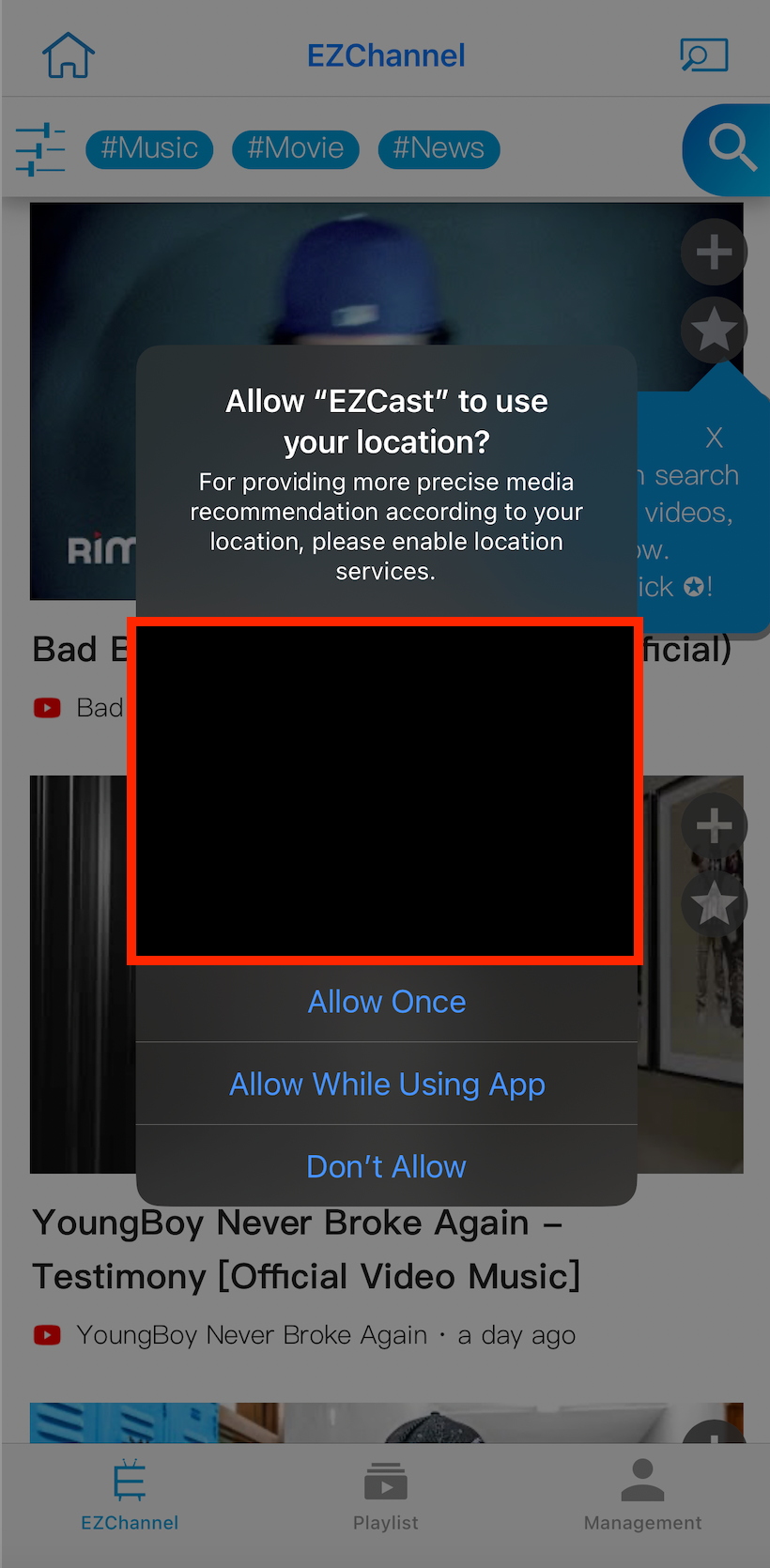
After doing all of this, I was able to mirror my screen from my iPhone to my monitor. It insisted it needed all of this data in order to mirror the screen from my phone to a monitor that I owned, via a cable that is physically connected between the two. It said it would share this data with advertisers, and that “If you are located outside China and choose to provide information to us, please note that we transfer the data, including Personal Data, to China and process it there” (it should be noted that China-based companies are required by law to store customer data in China, so perhaps this specific provision isn’t that odd or surprising, but the the privacy policy about my data ending up in China was refreshingly blunt.)
Almost anything I tried to do on the EZ Cast app required a permission of some sort, and ads for streaming services and other apps popped up almost anytime I clicked anything. The app also has its own specific embedded web browser, as well as a specific quasi streaming service called “EZChannel,” which is just an interface for playing YouTube videos, which also requires access to your location. The app also has a camera function that lets you doodle on images, for some reason. It also turned on four different analytics trackers, including something it calls “Google Analytics for dongles,” a term that, when Googled, returns nothing remotely useful.
While I was interested in getting this cable because I’m generally obsessed with weird cables and crappy gadgets, the existence of this adapter is actually particularly relevant given the FTC’s lawsuit against Amazon, which blasts the company for making its site harder to navigate and for placing tons of spammy ads where relevant search results used to be. A quick search shows various Reddit users who are confused by the QR code, some of whom said they bought the cable on Amazon. Bumstead is almost positive that the cord itself came from Amazon leftovers or returns. Amazon does have an EZCast store, but it’s not currently selling this specific cord, from what I can tell.
“A lot of recyclers end up with Amazon returns boxes, you can buy them for a certain amount of money from Amazon or their partners. They tend to have a bunch of cables on the bottom since they fall below the big items. So I’ve had recyclers dump the ‘crumbs’ into a single box and sell them to me.” Bumstead told me, adding that he had between 20 and 30 of these cords. “It’s pretty wacky stuff and lots of fun, you get bizarre gizmos you’ve never heard of, ie little robots that walk around when you plug their cable into usb, cables that glow in patterns, etc.”
“I should say I don’t know 100% it’s ALL originating from Amazon, but that’s what all the recyclers in question have told me and shown me when I was there,” he added. “Amazon does dump a lot of stuff that sellers have warehoused via FBA and choose not to have it sent back to them.”