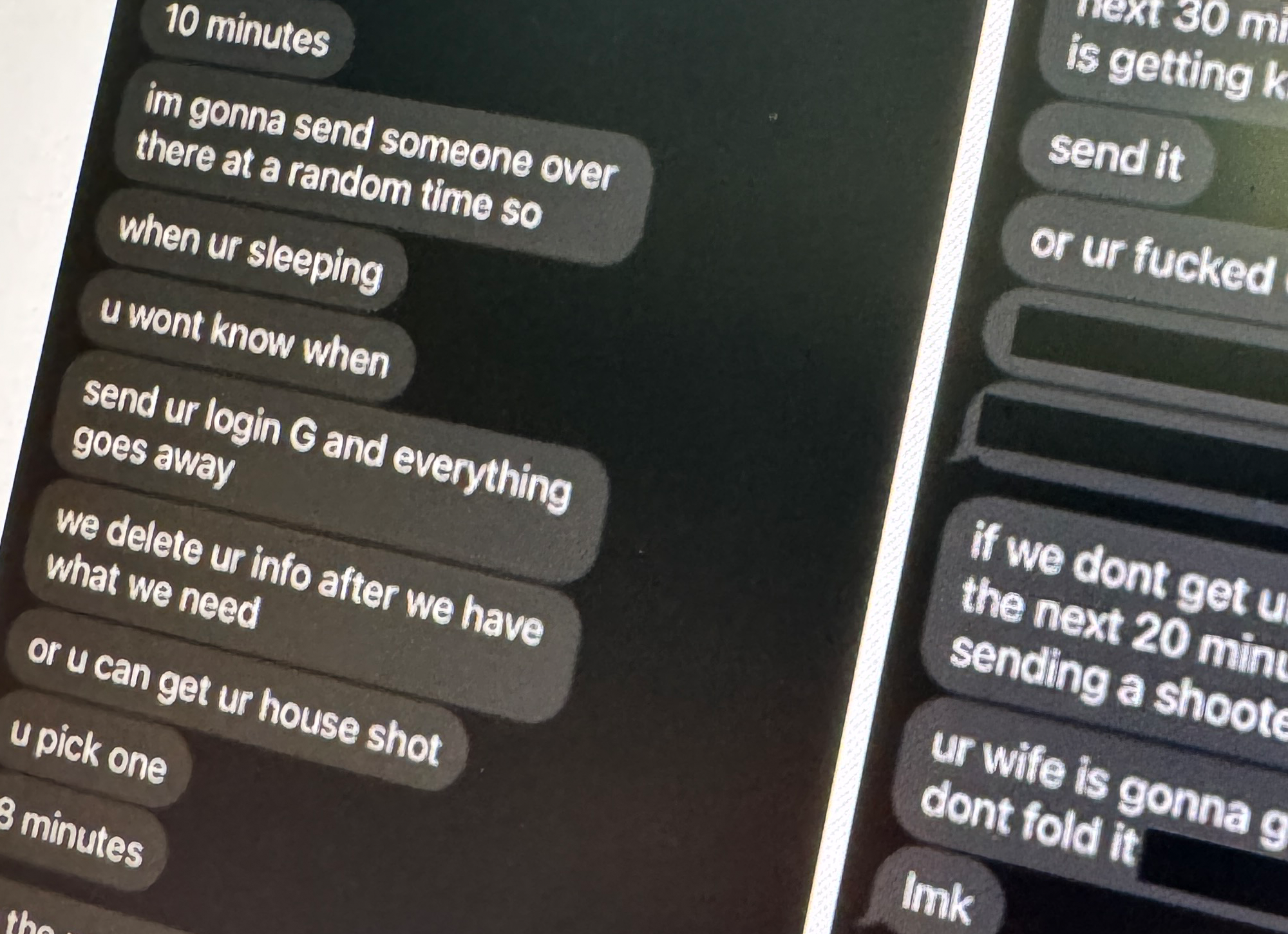
In a highly unusual marriage in the cybercrime underground, English-speaking members of “the Comm,” a wide spanning entity that includes SIM swappers and physically violent criminals, are working with the Eastern European ransomware group called ALPHV, two cybersecurity industry sources told 404 Media. 404 Media granted the sources anonymity to speak more candidly about developments in the cybercrime ecosystem. ALPHV is connected to the recent hack of MGM casinos.
The unlikely bedfellows make powerful partners in crime. Members of the Comm can be highly adept at social engineering, using their native English language skills to take over targets’ phone numbers or sweet talk their way into corporate systems. But they are also unusually audacious in their hacks, showing off their wealth or using threats of violence against targets that other, more stealthy hackers may avoid. Combine that brazenness with the highly professionalized world of Eastern European ransomware-as-a-service, and you have a new alliance that is wreaking havoc across all sorts of industries.