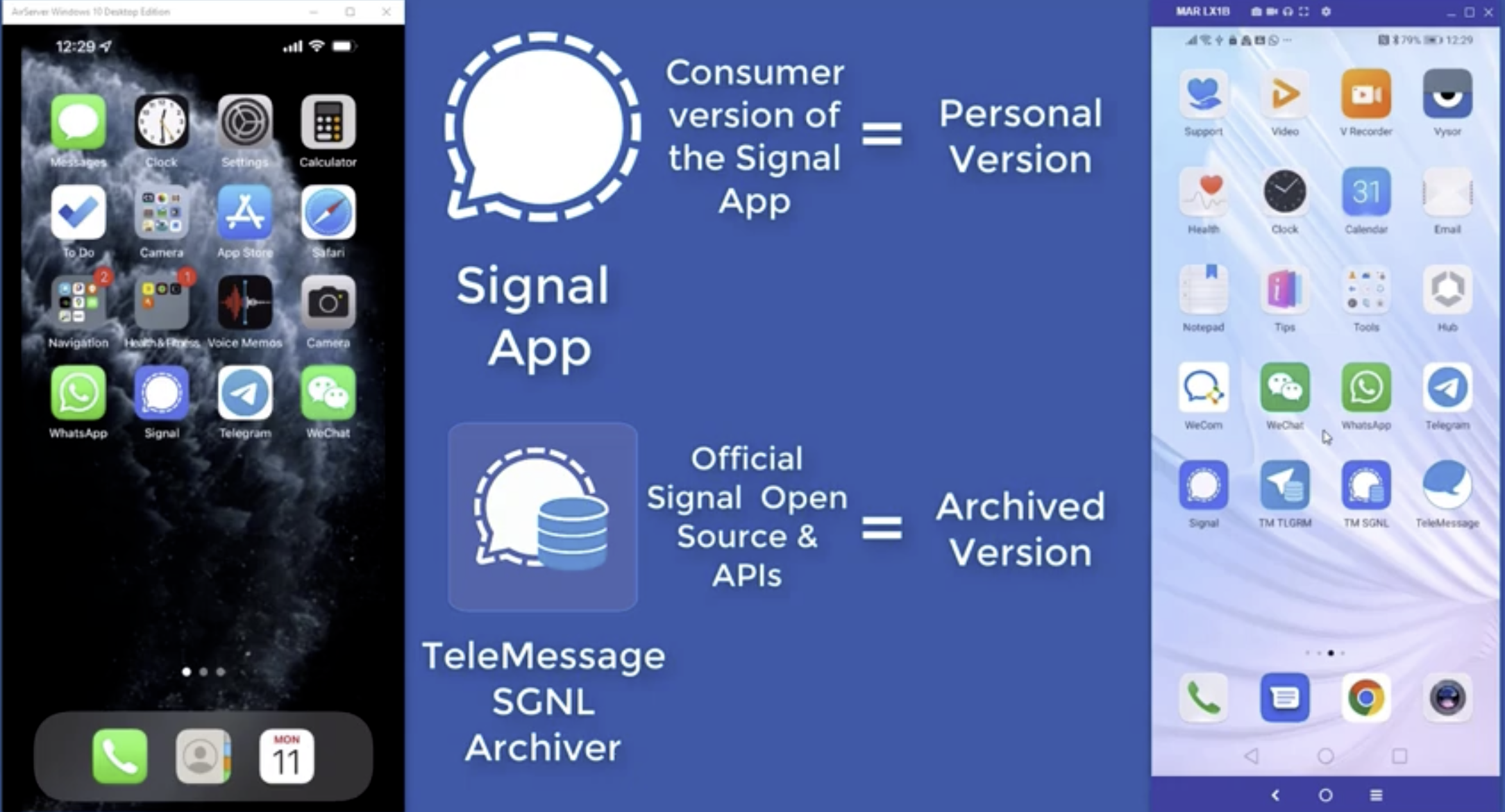
Earlier this week TeleMessage, the company that creates modified versions of messaging apps like Signal and adds an archiving ability to them, made a video private on its YouTube channel that explained how its Signal message archiving tool worked, and how the company says it is able to copy messages securely. The hiding of the video came after 404 Media revealed that a hacker had targeted TeleMessage, which is used by the Trump administration, and managed to obtain the contents of some users’ messages and group chats.
404 Media made a transcript of what this video said and is now publishing it in order to preserve TeleMessage’s claims around the security and functioning of its Signal archiving product. The news comes after Senator Ron Wyden has demanded a Department of Justice investigation into the TeleMessage episode, including the national security risk the app poses. The letter demanding the investigation also points to TeleMessage’s marketing material which claims messages are protected with end-to-end encryption, a claim that both the hack and a subsequent technical analysis refute.
The video said TeleMessage’s app keeps “intact the Signal security and end-to-end encryption when communicating with other Signal users.” This is not true, judging by the fact the hacker was able to obtain plaintext Signal messages. The video also says “The only difference is the TeleMessage version captures all incoming and outgoing Signal messages for archiving purposes.”