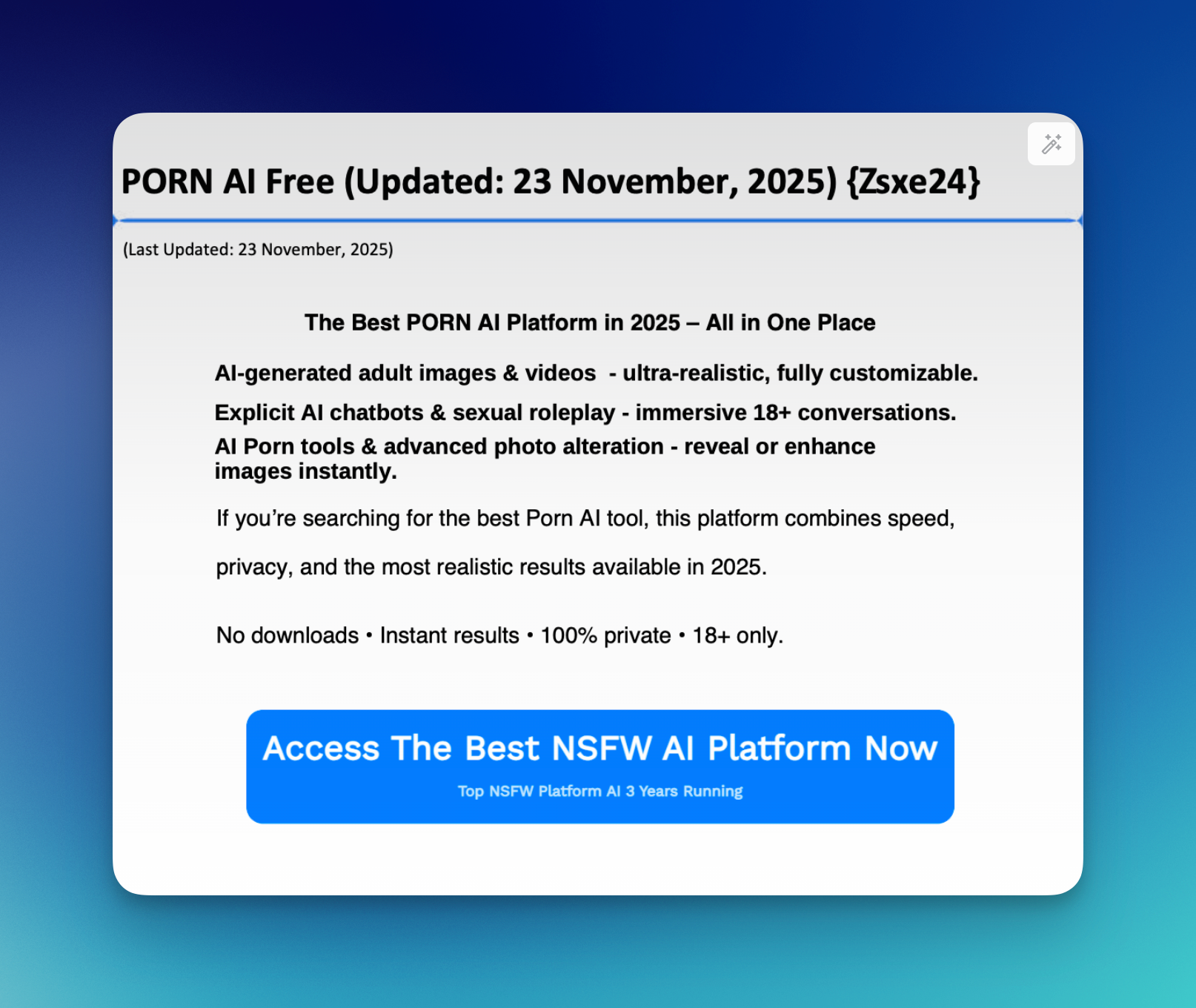
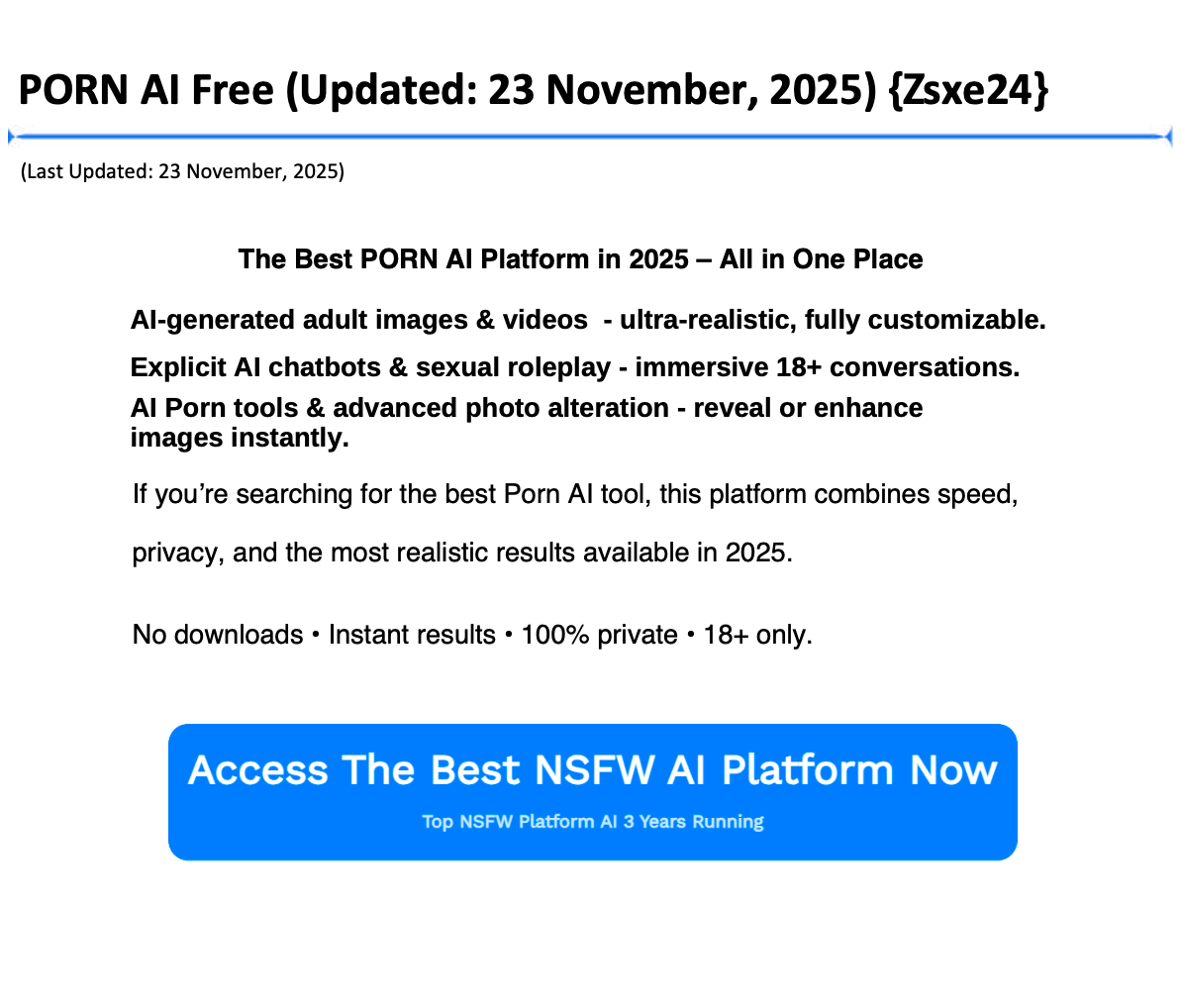
Dozens of government and university websites belonging to cities, towns, and public agencies across the country are hosting PDFs promoting AI porn apps, porn sites, and cryptocurrency scams; dozens more have been hit with a website redirection attacks which lead to animal vagina sex toy ecommerce pages, penis enlargement treatments, automatically-downloading Windows program files, and porn.
“Sex xxx video sexy Xvideo bf porn XXX xnxx Sex XXX porn XXX blue film Sex Video xxx sex videos Porn Hub XVideos XXX sexy bf videos blue film Videos Oficial on Instagram New Viral Video The latest original video has taken the internet by storm and left viewers in on various social media platforms ex Videos Hot Sex Video Hot Porn viral video,” reads the beginning of a three-page PDF uploaded to the website of the Irvington, New Jersey city government’s website.
The PDF, called “XnXX Video teachers fucking students Video porn Videos free XXX Hamster XnXX com” is unlike many of the other PDFs hosted on the city’s website, which include things like “2025-10-14 Council Minutes,” “Proposed Agenda 9-22-25,” and “Landlord Registration Form (1 & 2 unit dwelling).”
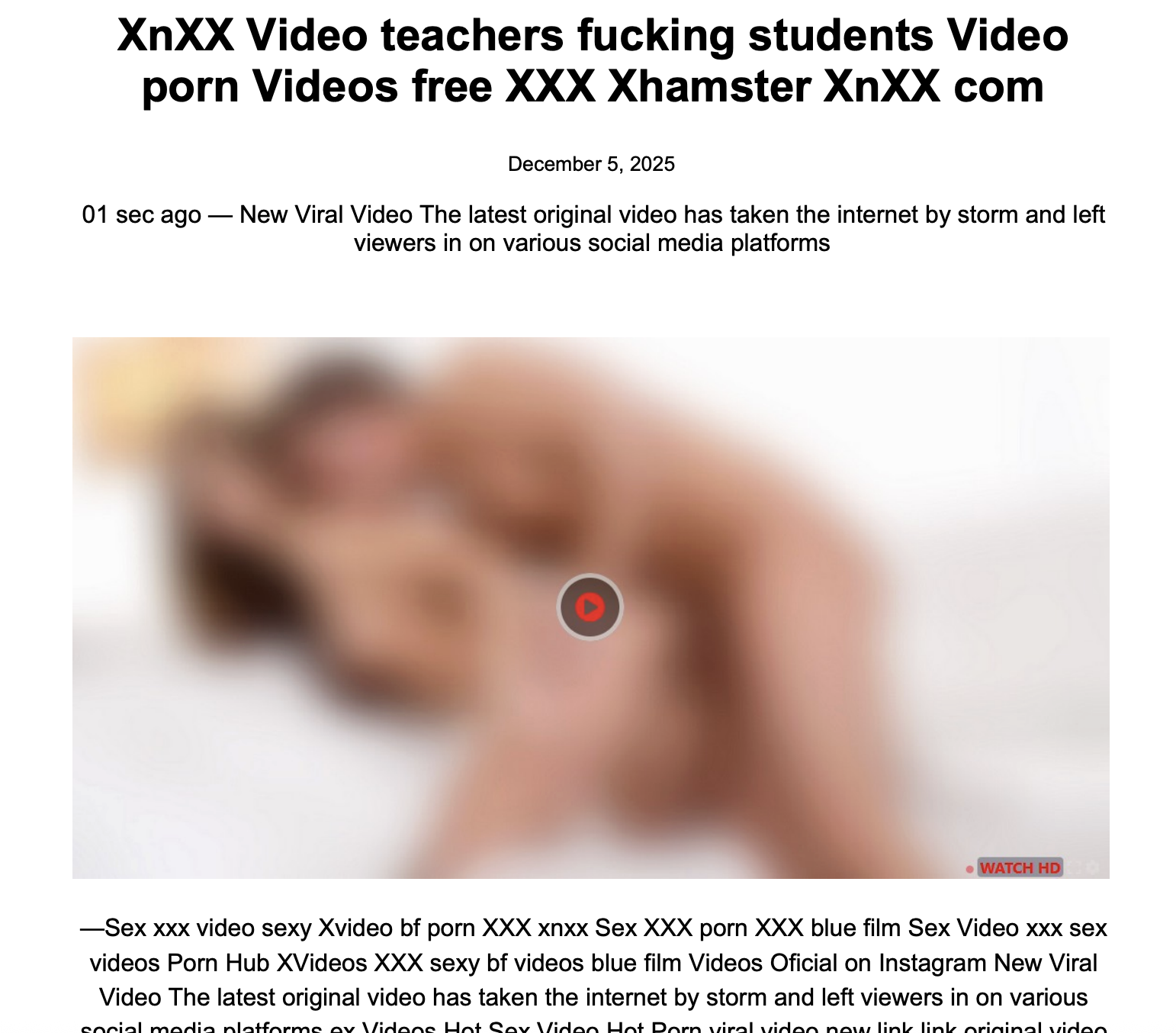
It is similar, however, to another PDF called “30 Best question here’s,” which looks like this:
Irvington, which is just west of Newark and has a population of 61,000 people, has fallen victim to an SEO spam attack that has afflicted local and state governments and universities around the United States.
Researcher Brian Penny has identified dozens of government and university websites that hosted PDF guides for how to make AI porn, PDFs linking to porn videos, bizarre crypto spam, sex toys, and more.
Reginfo.gov, a regulatory affairs compliance website under the federal government’s General Services Administration, is currently hosting a 12 page PDF called “Nudify AI Free, No Sign-Up Needed!,” which is an ad and link to an abusive AI app designed to remove a person’s clothes. The Kansas Attorney General’s office and the Mojave Desert Air Quality Management District Office in California hosted PDFs called “DeepNude AI Best Deepnude AI APP 2025.” Penny found similar PDFs on the websites for the Washington Department of Fish and Wildlife, the Washington Fire Commissioners Association, the Florida Department of Agriculture, the cities of Jackson, Mississippi and Massillon, Ohio, various universities throughout the country, and dozens of others. Penny has caught the attention of local news throughout the United States, who have reported on the problem.
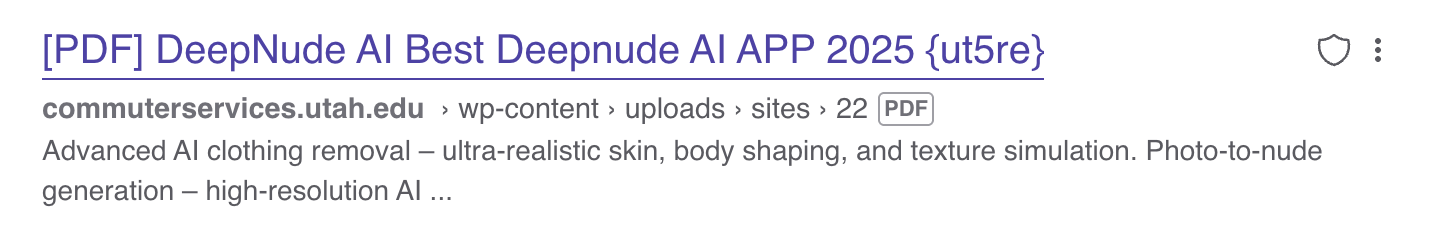
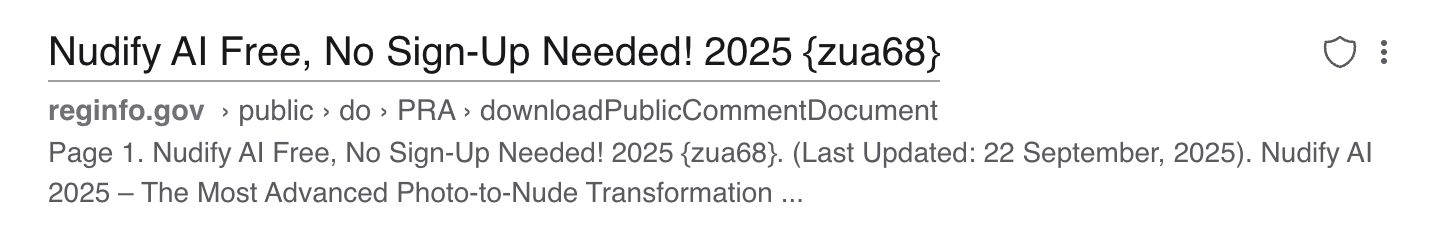
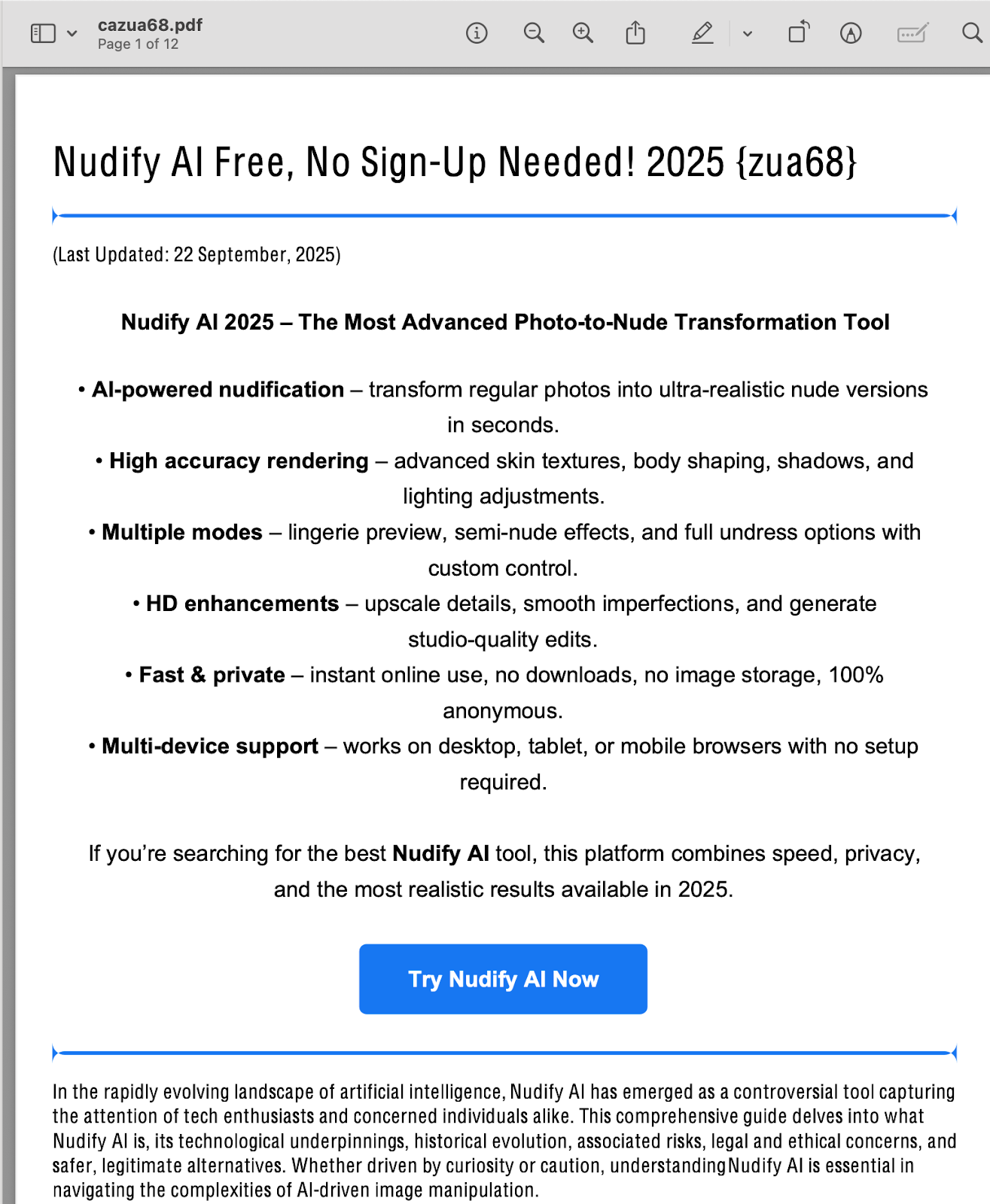
The issue appears to be stemming from websites that allow people to upload their own PDFs, which then sit on these government websites. Because they are loaded with keywords for widely searched terms and exist on government and university sites with high search authority, Google and other search engines begin to surface them. In the last week or so, many (but not all) of the PDFs Penny has discovered have been deleted by local governments and universities.
But cities seem like they are having more trouble cleaning up another attack, which is redirecting traffic from government URLs to porn, e-commerce, and spam sites. In an attack that seems similar to what we reported in June, various government websites are somehow being used to maliciously send traffic elsewhere. For example, the New York State Museum’s online exhibit for something called “The Family Room” now has at least 11 links to different types of “realistic” animal vagina pocket masturbators, which include “Zebra Animal Vagina Pussy Male Masturbation Cup — Pocket Realistic Silicone Penis Sex Toy ($27.99),” and “Must-have Horse Pussy Torso Buttocks Male Masturbator — Fantasy Realistic Animal Pussie Sex Doll.”
Links Penny found on Knoxville, Tennessee’s site for permitting inspections first go to a page that looks like a government site for hosting files then redirects to a page selling penis growth supplements that features erect penises (human penises, mercifully), blowjobs, men masturbating, and Dr. Oz’s face.
Another Knoxville link I found, which purports to be a pirated version of the 2002 Vin Diesel film XXX simply downloaded a .exe file to my computer.
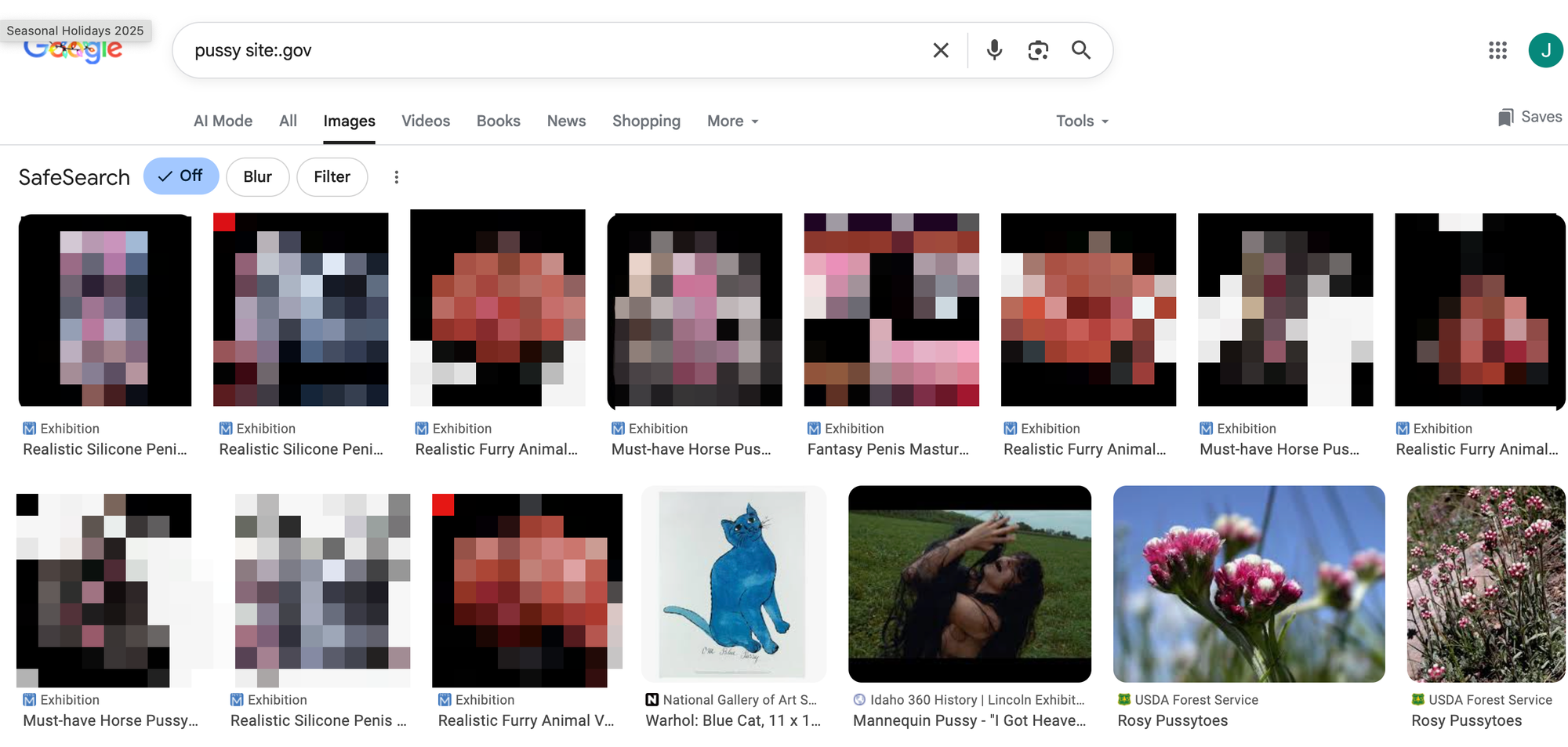
Penny believes that what he has found is basically the tip of the iceberg, because he is largely finding these by typing things like “nudify site:.gov” “xxx site:.gov” into Google and clicking around. Sometimes, malicious pages surface only on image searches or video searches: “Basically the craziest things you can think of will show up as long as you’re on image search,” Penny told 404 Media. “I’ll be doing this all week.”
The Nevada Department of Transportation told 404 Media that “This incident was not related to NDOT infrastructure or information systems, and the material was not hosted on NDOT servers.This unfortunate incident was a result of malicious use of a legitimate form created using the third-party platform on which NDOT’s website is hosted. NDOT expeditiously worked with our web hosting vendor to ensure the inappropriate content was removed.” It added that the third-party is Granicus, a massive government services company that provides website backend infrastructure for many cities and states around the country, as well as helps them stream and archive city council meetings, among other services. Several of the affected local governments use Granicus, but not all of them do; Granicus did not respond to two requests for comment from 404 Media.
The California Secretary of State’s Office told 404 Media: “A bad actor uploaded non-business documents to the bizfile Online system (a portal for business filings and information). The files were then used in external links allowing public access to only those uploaded files. No data was compromised. SOS staff took immediate action to remove the ability to use the system for non-SOS business purposes and are removing the unauthorized files from the system.” The Washington Department of Fish and Wildlife said “WDFW is aware of this issue and is actively working with our partners at WaTech to address it.” The other government agencies mentioned in this article did not respond to our requests for comment.