A group of hackers gained access to the backend of an AI chatbot that fast food franchises use to help automate hiring. The researchers were seemingly able to accept or reject specific job applicants, and had access to a wealth of sensitive information on applicants, the fast food franchises, and the AI company itself, called Chattr.
MrBruh, one of the researchers involved, told 404 Media in an email that the access could have been used to ransom the data. That is, “nuke the DB [database] then ask for money if they want it back.”
“I'm just glad I managed to nip it in the bud,” they added. MrBruh said they reported the issue to Chattr.
Chattr advertises itself as “the first ever automated end-to-end hiring software for the hourly workforce powered by an AI digital assistant.”
MrBruh wrote in a blog post about the issue that this episode started with a script he had written to scan for exposed Firebase credentials from companies that use the .ai TLD. Firebase is a backend platform commonly used by app developers. MrBruh’s suspicion, he wrote, was that in the ongoing AI product rush, “someone would take a shortcut and forget to implement proper security rules.”
The script returned a Firebase configuration for what appeared to relate to fast food chain KFC. The researchers took that configuration and put it into Firepwn, a tool available on Github used for testing the security of apps using Firebase. At first, the researchers didn’t have the ability to read any of the data stored. But after creating a new user account through Firebase, they gained read and write access to the underlying database.
This revealed a wealth of data, including names, phone numbers, email addresses, location of branches, messages, work shifts, and some passwords, according to MrBruh’s blog post. The data related to franchisee managers, job applicants, and employees of Chattr, the chatbot platform which the Firebase instance related to.
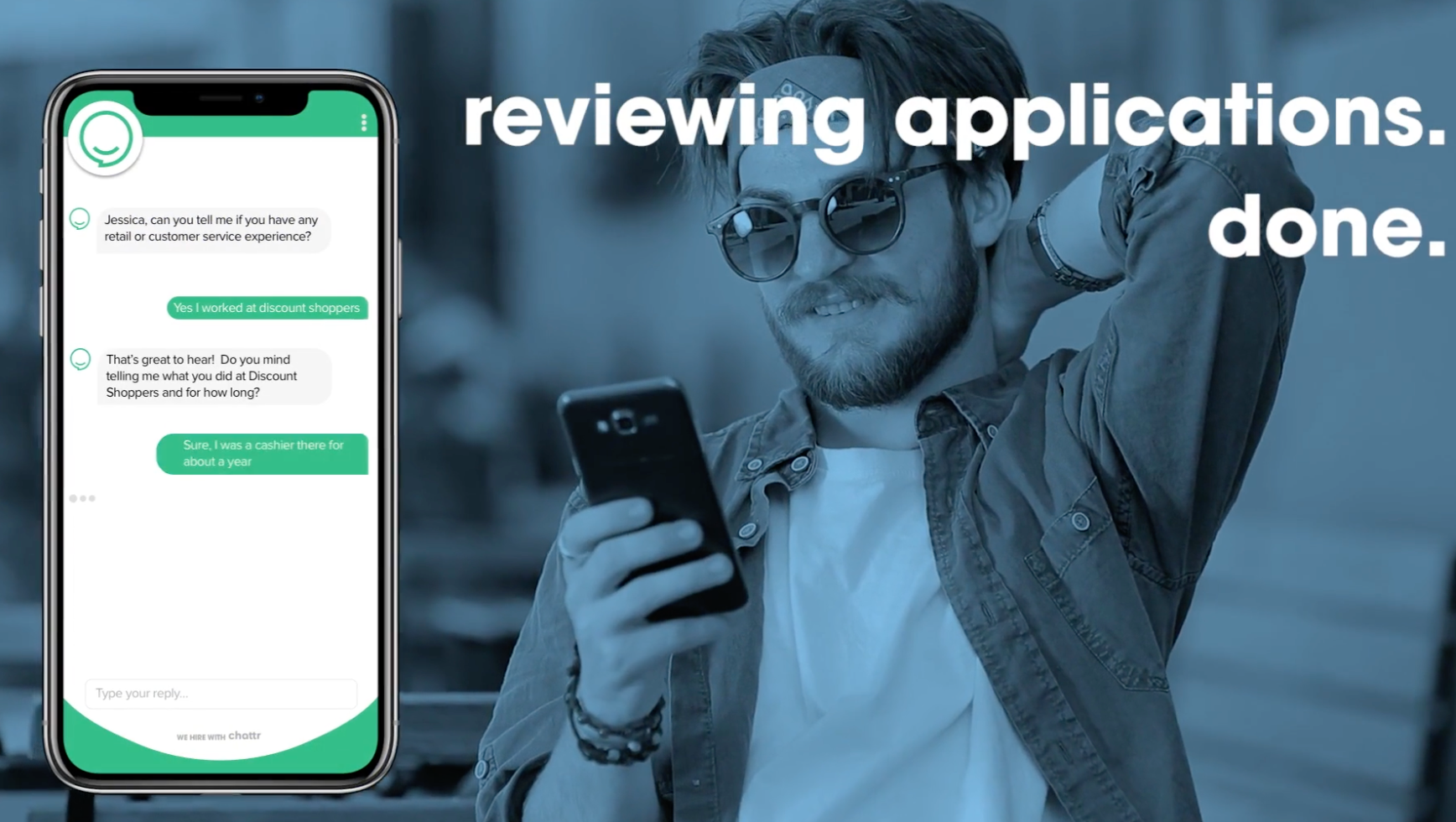
“We’ve reinvented hourly workforce hiring with an AI assistant that easily handles the tedious tasks while personally guiding applicants through an experience they’ll love,” a promotional video for Chattr explains. “Reviewing applications, done. Scheduling interviews? Done. Background checks? Yep, you guessed it, done.”
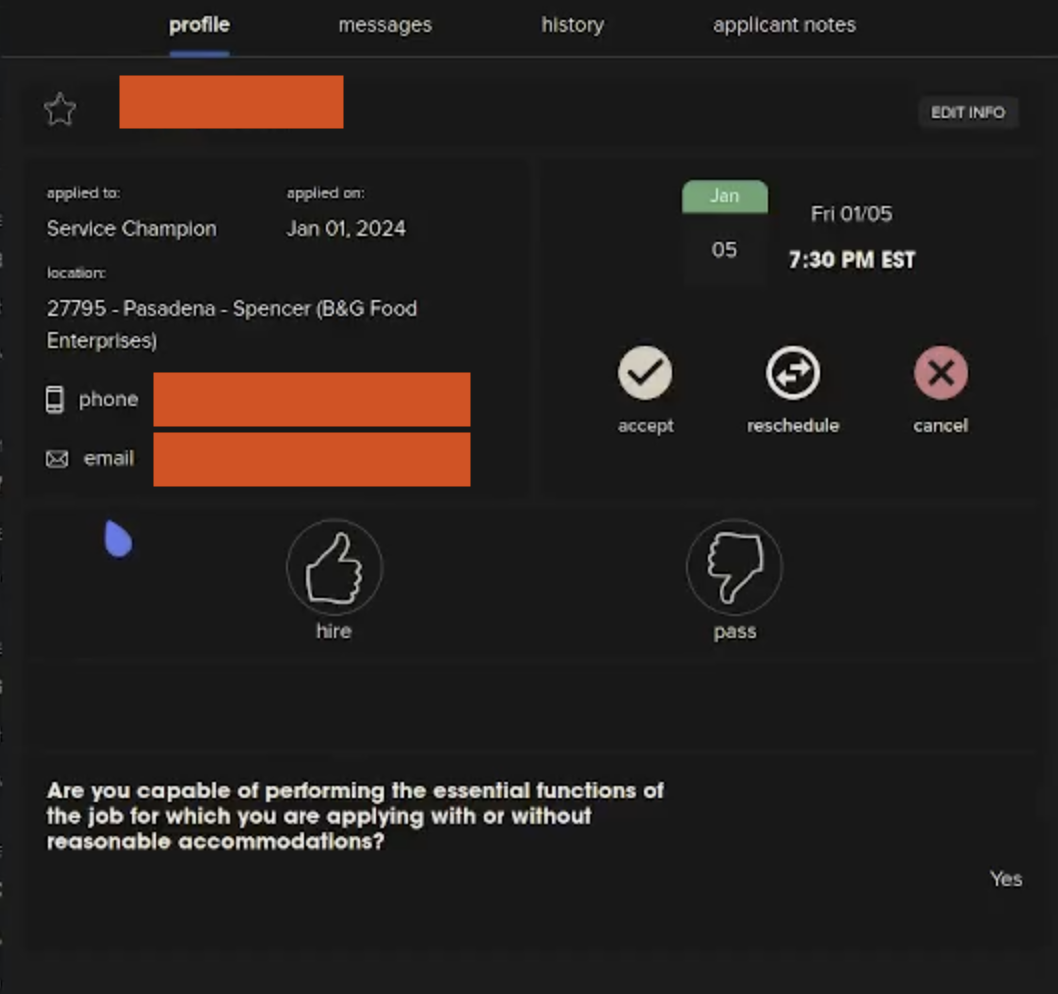
But the data exposure was not limited to a single set of KFC data. The researchers found they were able to access an administrator dashboard, revealing a list of organizations using Chattr and granting the ability to accept or deny job applicants, as well as refund payments made to Chattr, MrBruh writes.
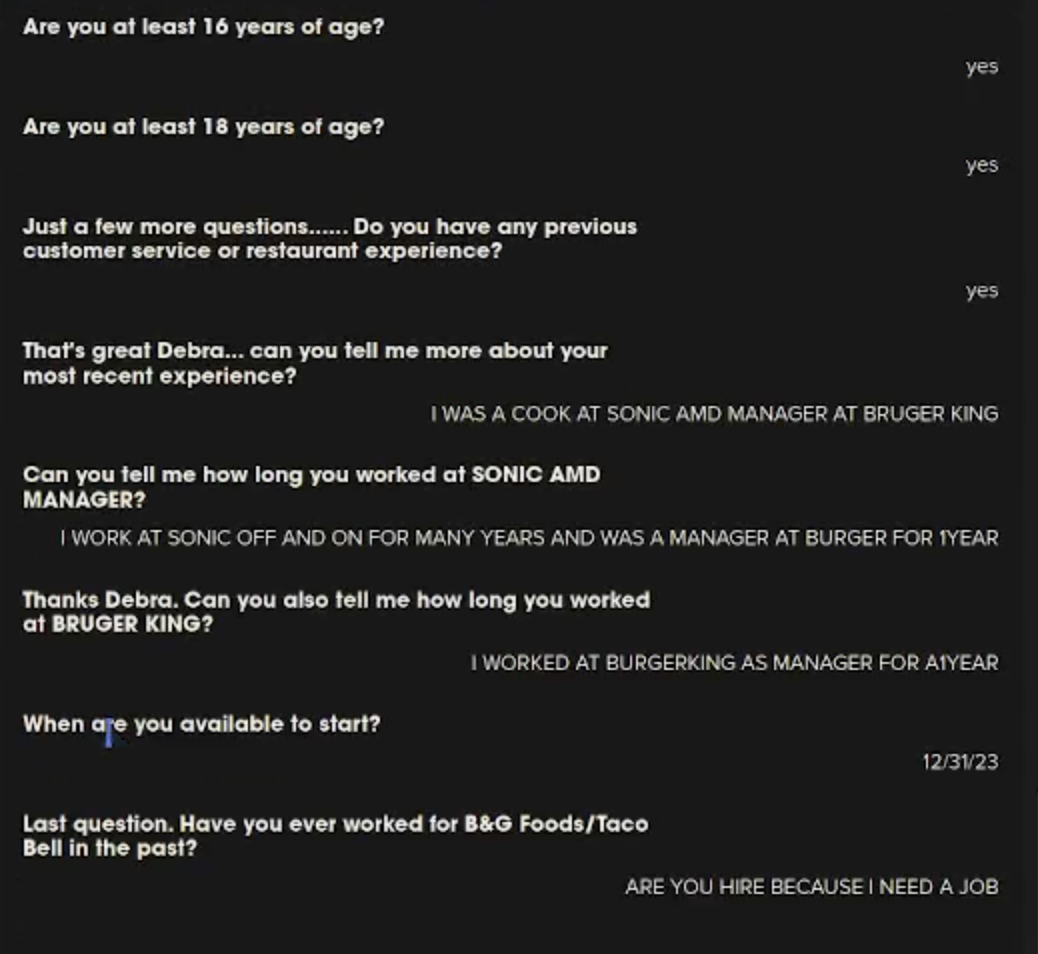
MrBruh shared an extended, 30-minute video with 404 Media of the researchers exploring the data access. The video shows a researcher freely clicking through the Chattr backend, flicking between users, organizations, and details on specific applicants. Some organizations mentioned in that video include Chick-fil-A locations, Subway, and many other smaller companies. Chick-fil-A and Subway did not respond to a request for comment. In that video, logs of a conversation appear to show the chatbot automatically denying an applicant based on certain criteria.
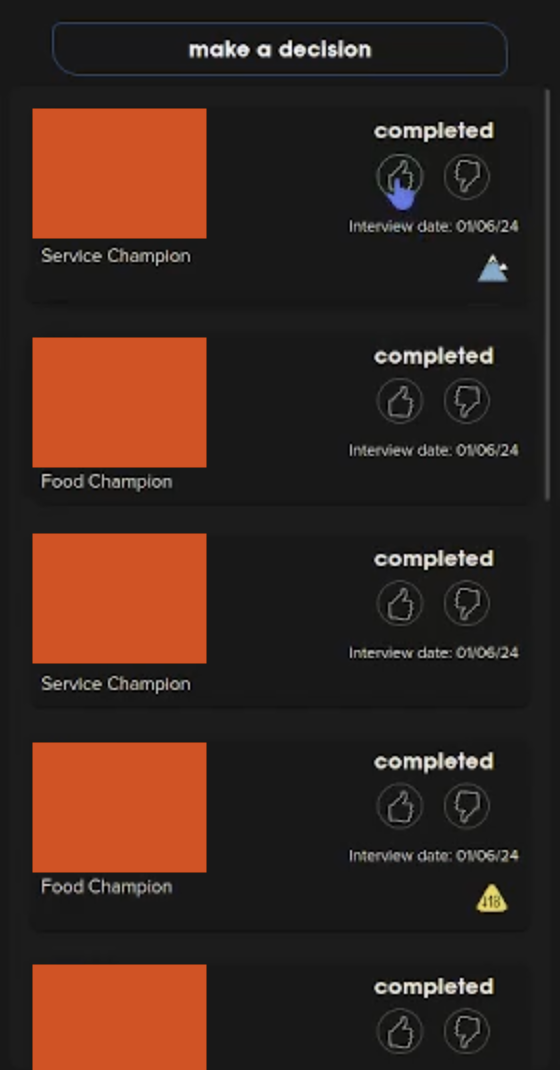
In their blog post, MrBruh posted multiple screenshots which appear to show conversations between job applicants and Chattr’s bot; upcoming interview dates, and a column marked as “make a decision” with the names of apparent applicants and a thumbs up, thumbs down interface.
Eva, one of the other researchers involved, wrote on their own blog “we were in a call at the time, and our reaction to this was insane.”
MrBruh wrote that they disclosed the vulnerability on January 9. A day later, Chattr fixed the issue and the support ticket was closed, with “no thanks or further contact received despite explicitly requesting it,” MrBruh wrote. Chattr also did not respond to a request for comment from 404 Media.
KFC told 404 Media in an email that Chattr only works with one KFC franchisee. “Chattr is not a vendor affiliated with KFC Corporation. They work with one franchisee only and we are not privy to any details of that arrangement,” the spokesperson wrote.